Red teaming
Castor Security specializes in providing cutting-edge red teaming services that are tailored to meet the unique needs of each client. Our team of experts is known for their custom tooling, advanced persistent threat (APT) simulation capabilities, and modern evasion techniques to simulate real-world cyber attacks and identify vulnerabilities in your organization’s security posture.
With our custom tooling, we can create specialized attack vectors that mimic the tactics, techniques, and procedures used by sophisticated threat actors. This allows us to test your defenses against the latest cyber threats and ensure that your security controls are effective in detecting and mitigating potential attacks.
Our APT simulation services go beyond traditional penetration testing by emulating the tactics of advanced adversaries. By simulating the behavior of threat actors with nation-state capabilities, we can provide a more realistic assessment of your organization’s security resilience and readiness to defend against targeted attacks.
Vulnerability research
Testing can show the presence of bugs, but not their absence.
Edsger W. Dijkstra
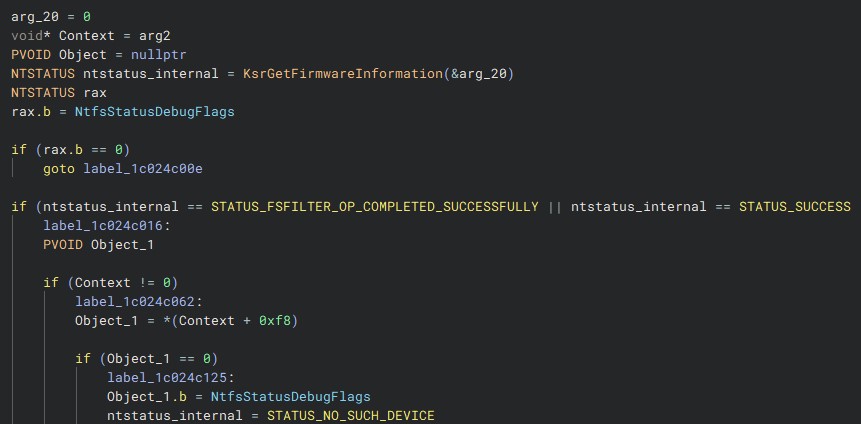
We are at the forefront of vulnerability research, utilizing a combination of advanced techniques such as fuzzers, static code analysis, and reverse engineering to uncover security weaknesses in software and systems. Our dedicated team of researchers is skilled in leveraging these tools to identify and mitigate vulnerabilities before they can be exploited by malicious actors.
Fuzzers play a crucial role in our vulnerability research process by automatically generating a large volume of invalid, unexpected, or random data inputs to test the robustness of software applications. By subjecting programs to fuzz testing, we can uncover potential bugs, crashes, or security vulnerabilities that may not be apparent through traditional testing methods.
Static code analysis is another powerful tool in our arsenal, allowing us to analyze source code without executing the program. By scanning code for potential security flaws, memory leaks, or other issues, we can proactively identify vulnerabilities and recommend remediation strategies to improve the overall security posture of the software.
Reverse engineering is a key technique employed by our researchers to dissect and understand the inner workings of software and firmware. By deconstructing binaries and examining their behavior, we can uncover hidden vulnerabilities, backdoors, or malicious code that may pose a threat to the security of the system.